On the Subject of A Password Module That Shouldn't Be Touched
This thing is not as secure as 256-bit security, I think.
In order to solve the module, a password is required to be entered in the input phase.
Preface
- F1 will serve as a submit/stage-advance button.
- F2 clears your input.
Activating The Module
If Bamboozled Again, Ultimate Cycle, or UltraStores is present, the input is simply *dead*. This can be inputted using "88DDEEAADD88".
Otherwise, take the serial number, convert the digits using A0Z25 (table for convenience), and convert everything to lowercase. You can input this by pressing each letter twice on the module.
For example, "UX4TA2" would be inputted as "UUXXEETTAACC".
| Digit | 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 |
|---|---|---|---|---|---|---|---|---|---|---|
| Letter | a | b | c | d | e | f | g | h | i | j |
Stage Phase
The module's representation of the increase factor (I) can be anywhere from base 5 to base 16. You can use the base converter below to convert from some specified base back to decimal. Case does NOT matter in the boxes.
(If the result is -1, the input is invalid.)
The calculated value for a stage is calculated with the formula:
C = I + (TFA % 9) + (BT % 60 + ET % 60)
- C is the calculated value.
- I is the average increase factor, in base-10.
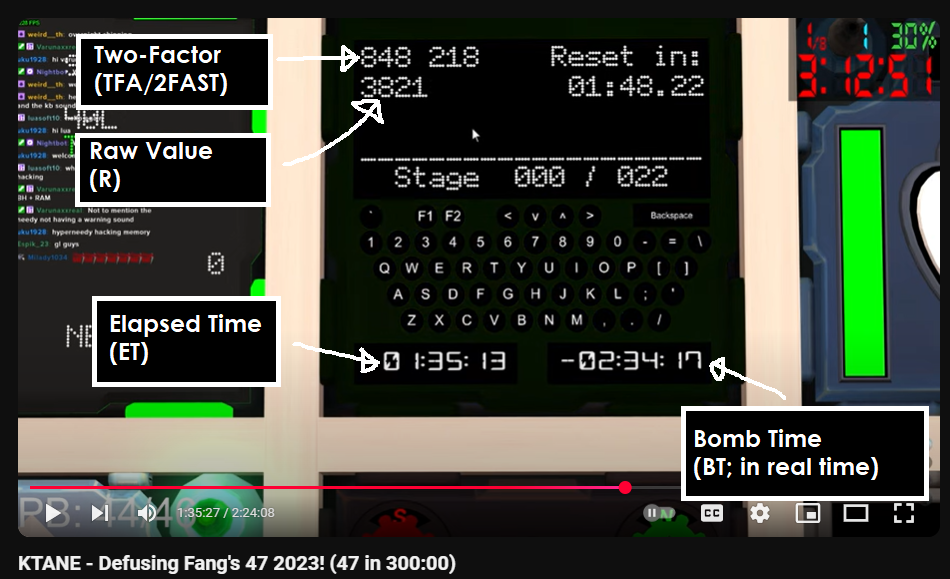
- TFA is the 2FAST, in the top-left.
- BT is amount of bomb time remaining in real time upon advancing from this stage, in the bottom-right.
- ET is elapsed time since the module initialized upon advancing from this stage, in the bottom-left.
A stage regenerates its information every 2 minutes, so work quickly.