On the Subject of Unfair’s Revenge
Now it’s more unfair because it took 2 months for him to create only to receive backlash, and another month to make sure he didn’t screw up any more than that.
The display on top shows the encrypted message. There’s also a strip of LEDs underneath the display which will light up to show the current stage the defuser is on.
The display on the right can be clicked to toggle between showing the Module ID, in white, or strikes the module is keeping track of, in red. Both of these are shown in Roman numerals.
For all operations involving STRIKES, always refer to the number in red on the module itself.
The module encrypts a string of four repeatable three-letter-long instructions with four different ciphers, using different keys for each. Enter the correct combination of inputs to disarm the module.
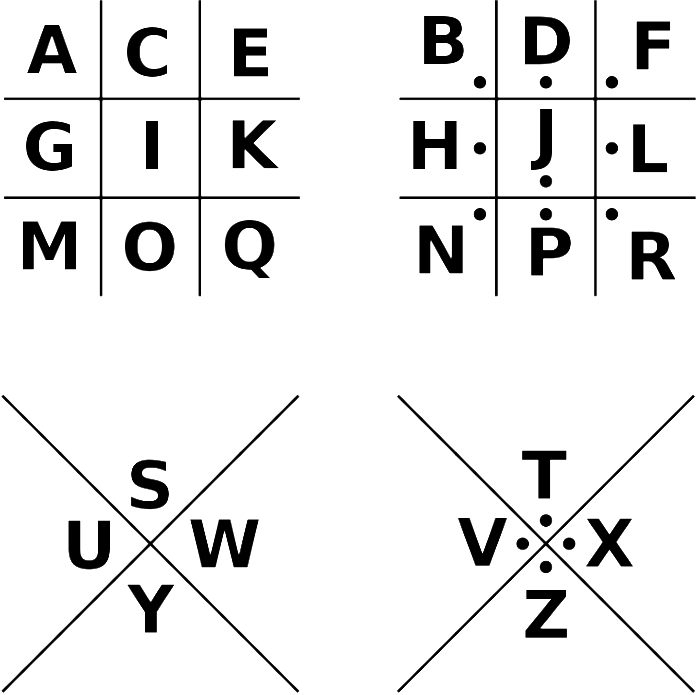
ALL ciphers referring to the alphabetical position refers to the A1Z26 standard for each letter unless stated otherwise.
- The basic order of the given encrypted text is the following: Original -> Playfair Ciphered -> Affine Ciphered -> Caesar Ciphered -> Pigpen Ciphered. Reverse the order to obtain the original instruction string.
Key A
- Start with the bomb’s first 3 serial number characters.
- Interpret each character from this set as a base-36 digit.
- If the character is unfamiliar in the set of base-36 digits, interpret this character as the digit “I”.
- Convert this base-36 number into decimal. Use Appendix Base-36 Conversion in case for reference. You will need to prepend this to the result of the next step.
- Grab the bomb’s last 3 serial number characters and transform each letter into its numerical equivalent (A = 1, B = 2, etc.).
- Make this a single string of digits.
- Append the result from converting the base-36 value with the modified string from step 4. Interpret this as one number.
- Convert this number into hexadecimal. Refer to Appendix D3K2H3X for instructions.