On the Subject of Unfair’s Legacy Cruel Revenge
He made two versions of Unfair’s Revenge because he wanted something more unfair than just the base idea... Was it unfair enough in the first place?
To distinguish this from Unfair Cipher and Unfair’s Revenge, the 2 displays on this module are identical with one of them being rotated. The display on top shows the encrypted message. There’s also a strip of LEDs underneath which will light up to show the current stage the defuser is on.
The display on the right can be clicked to cycle between showing the Module ID, in white, strikes the module is keeping track of, in red typically, and the extra keys. The Module ID and the strike counter are either shown in fixed or broken Roman numerals (VII, IX, IIII, ...), or in Arabic form. (1, 2, 3, 5, ...) Refer to Roman Art for a reference to Broken and Fixed Roman Numerals. Zero (0) in Fixed/Broken Roman Numerals will be shown as literally nothing on the module and “0” in Arabic form.
For all operations involving STRIKES, always refer to the number on the second screen on the module itself.
The module encrypts a string of six distant three-letter-long instructions with different ciphers, using different keys for each. Enter the correct combination of inputs to disarm the module.
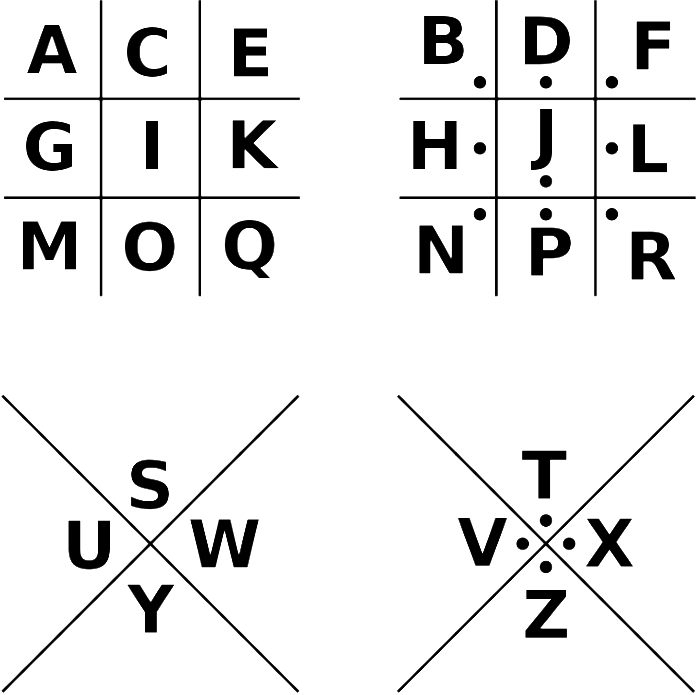
ALL ciphers referring to the alphabet refers to the A1Z26 standard for each letter unless stated otherwise. Alphabetical order is ALSO modified for the ciphers!
- The basic order of the given encrypted text is the following: Original -> 5x Ciphers -> Pigpen Ciphered. Reverse the order to obtain the original instruction string.
The next pages will go over instruction on how to decrypt the legacy version of Unfair's Cruel Revenge. If some information is not missing on the module, the defuser may have disabled Legacy Unfair's Cruel Revenge. Check the other manual on how to disarm that. You will know if you have legacy Unfair's Cruel Revenge disabled if the following is false: The 4th page is empty except with “=LEGACY=” at the bottom; Page 3 on the module has 2 sets of information dashed out.